
許家維 博士 (Dr. Chia-Wei Hsu, Vic Hsu)
Office:
TWISC@NCTU, DSNS Lab
國立交通大學網路安全實驗室
(at EC 622)
Ext:
03-5712121#54808
Contact at:
ⓗⓢⓤⓒⓦ@ⓒⓢ.ⓝⓒⓣⓤ.ⓔⓓⓤ.ⓣⓦ
許家維 (Chia-wei Hsu) received the M.S. and Ph.D. degrees from
National Chiao Tung University (NCTU), Hsinchu, Taiwan,
in 2009 and 2017, respectively.
He is currently a researcher in TWISC@NCTU.
His research focuses on computer security,
mobile security, virtual machine, and machine learning.
Research
Dynamic Multi-Tasks Learning for Malware Detection
Group Member: Shen-Chieh Lan
Malware detection needs much more information to build up a comprehensive
view of program behaviors. However, sophisticated malware usually equips
analysis-resistant techniques to evade detection. Analysts need to
devise new inspection methods for feature extraction. Since the
features used for model training against malware is always varying,
a dynamic approach to adding new features or new malware type is desirable.
We propose a evolvable detection model that extends its detection
capability over time.
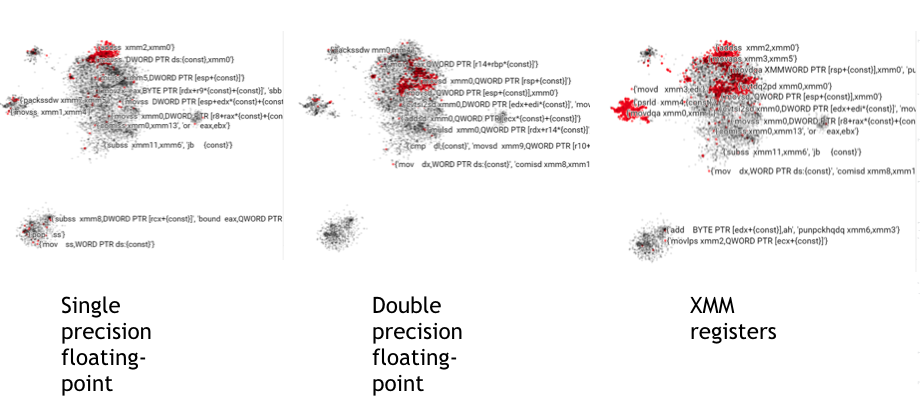
Learning Instruction Embeddings from Binaries
Group Member: Yang-Ting Chiang, Shen-Chieh Lan
Any first step for machine learning is to vectorize the data.
Instructions represent a complete scope of program behaviors,
but how to vectorize them is a difficult thing. To address this
problem, we apply the same idea from Word Embedding, which maps
discrete data to a high-dimensional space. However, using one-hot
as the initial vectors faces storage explosion in instruction sets.
We apply bloom-filter to achieve affordable space demand.
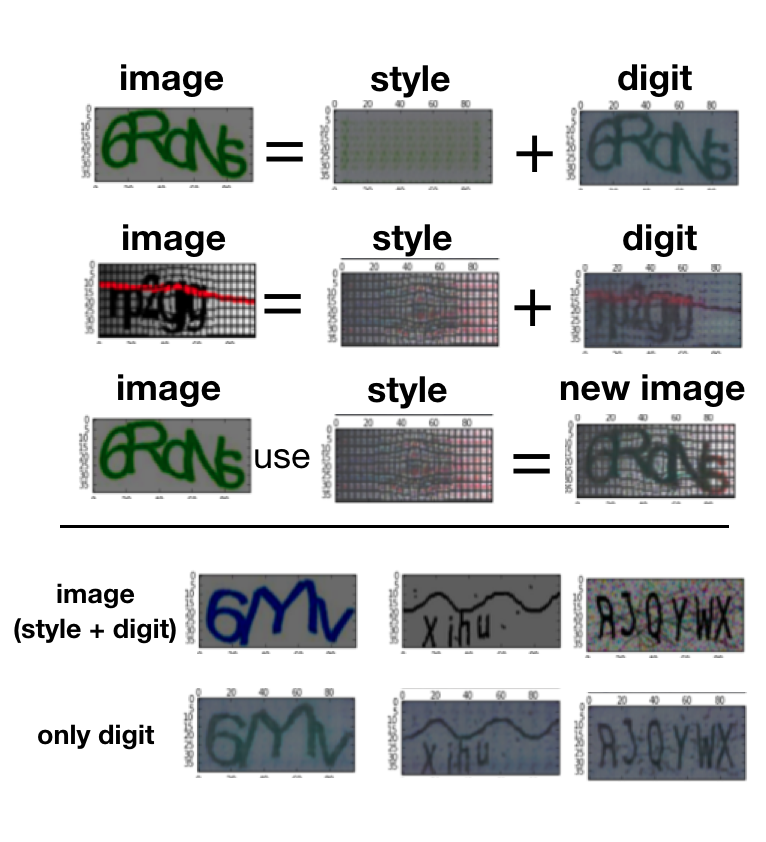
CAPTCHA Solver by Style Elimination
Group Member: Yun-Chih Kuo
We try to apply domain-adversarial learning to reduce the
recognition error through distinguish digit part from the
noise generated by various CAPTCHA styles. In our experiment,
our CAPTCHA solver can eliminate styles and synthesize a new
image with specified CAPTCHA styles.
Automatic ICC Data Reconstruction
Group Member: Shen-Ru Wei
To provide a comprehensive view, we propose Finder, an automatic ICC
data reconstruction system, for recovering system runtime information.
Finder automatically generates data resolvers corresponding to
communication types through transpiling.
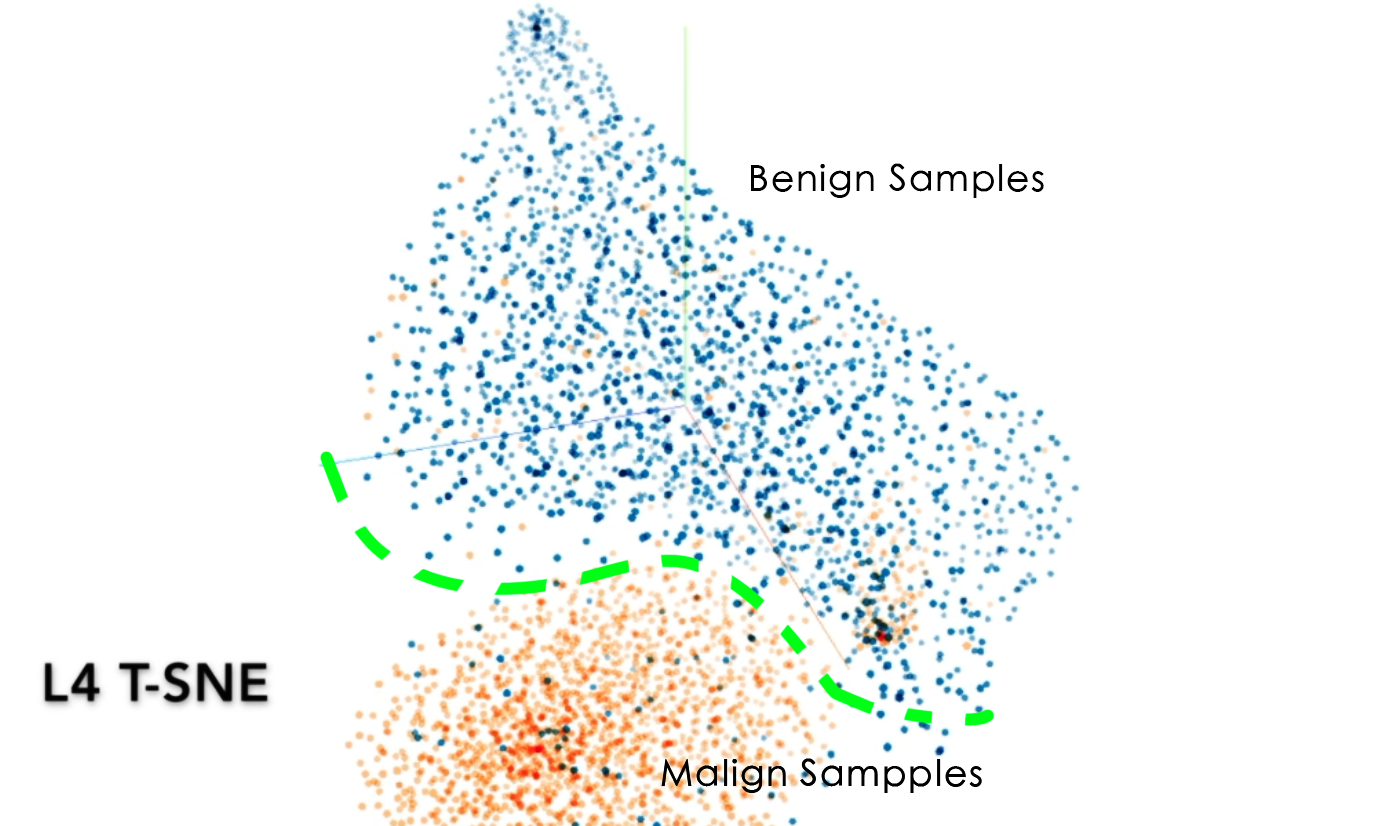
Semantics Modeling with Progressive Distillation
Group Member: Zong-Xian Shen
Our proposed scheme can generate discriminative models
against the repacked malicious apps.
These representative models of
malicious semantics can be progressively distilled with malign and
benign samples.
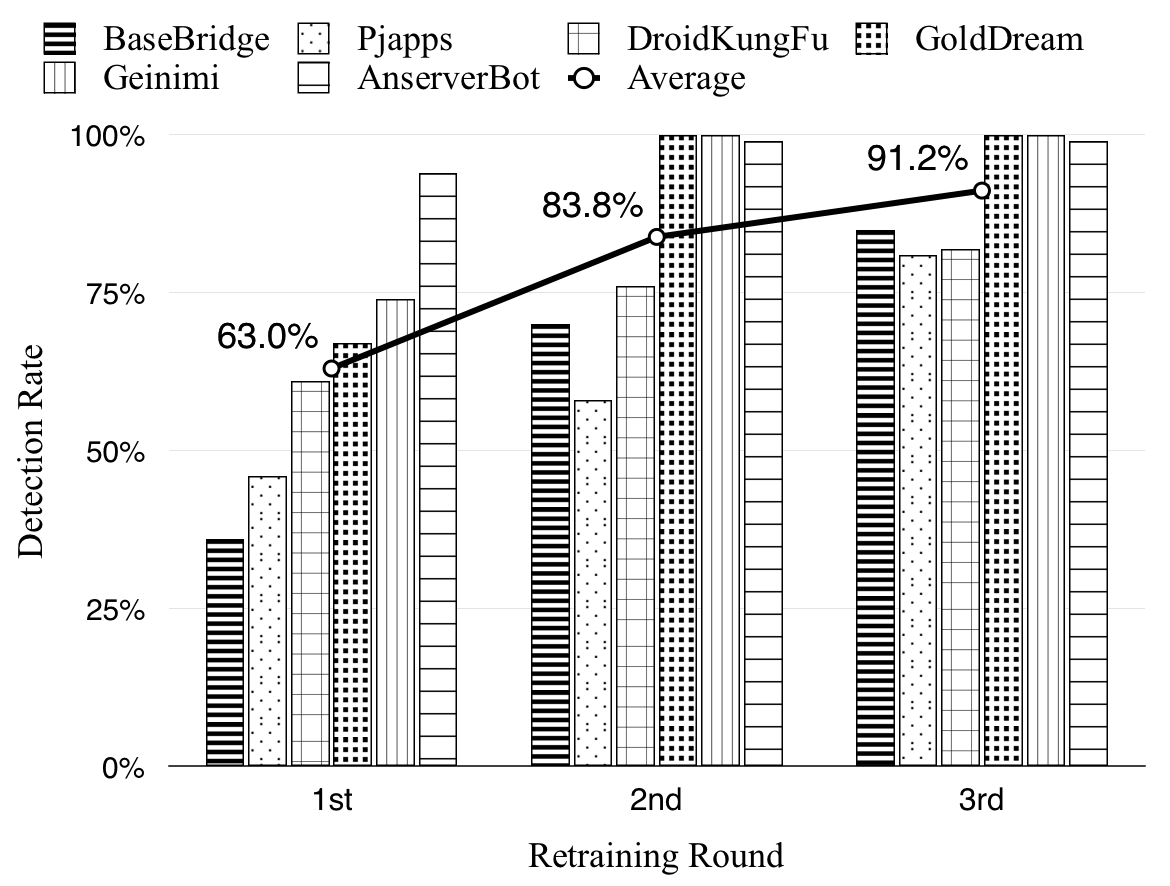
Our experiment shows that, after two retraining rounds,
Petridish achieved an average of 28 percent progressive detection
improvement from 63 to 91.2 percent for the large families,
exceeding 38 test samples in size.
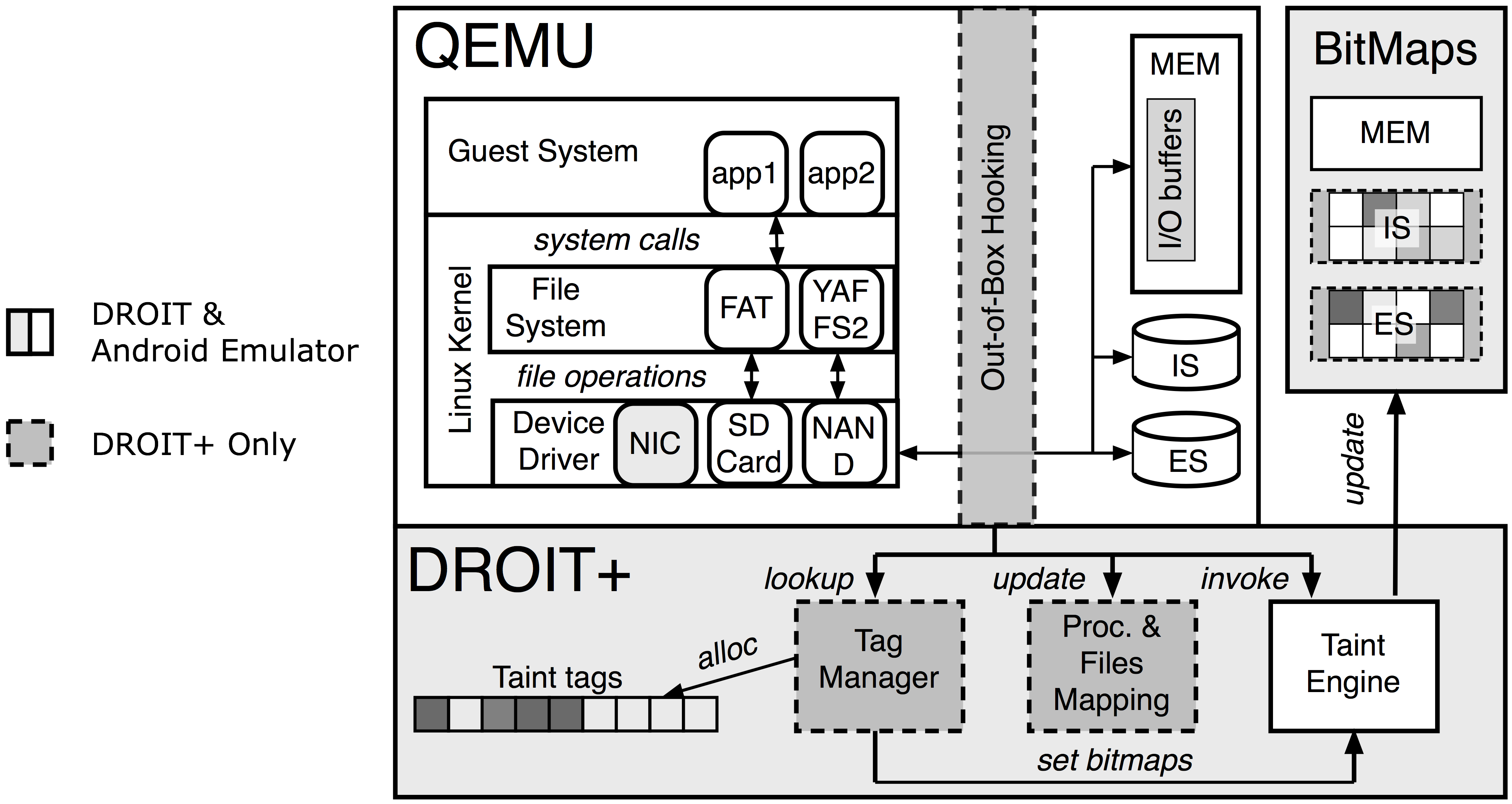
Taint Tracking for Storage Access on Android
Group Member: Chia-Huei Chang
The off-the-shelf taint tracking systems lack byte-granularity
support for storage tracking. We propose a fine-grained storage
tracking technique to track
data flow among Android storage. DROIT+ is able to reveal the
composition of data flows. Storage tracking on Android is difficult
since data flows of apps may span heterogeneous media including
memory, SD cards, NAND Flash, and network adapters.
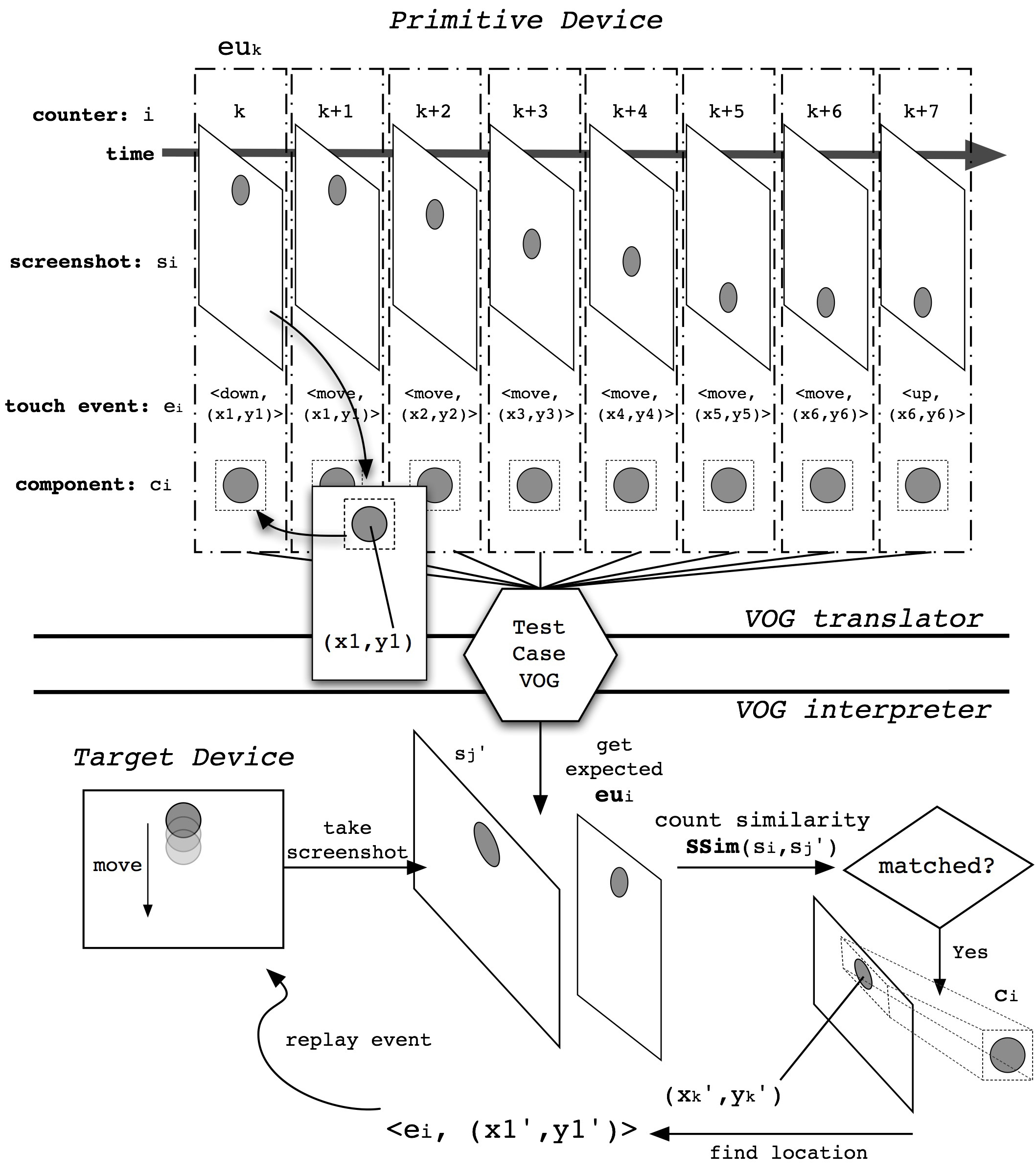
Adaptive Virtual Gestures for GUI Testing
Group Member: Shan-Hsin Lee
The wide variety of smartphones might diminish app quality
owing to insufficient testing. To complement in-depth testing,
a proposed breadth-first approach employs fast, automated
GUI testing for adaptive virtual gestures on various mobile devices.
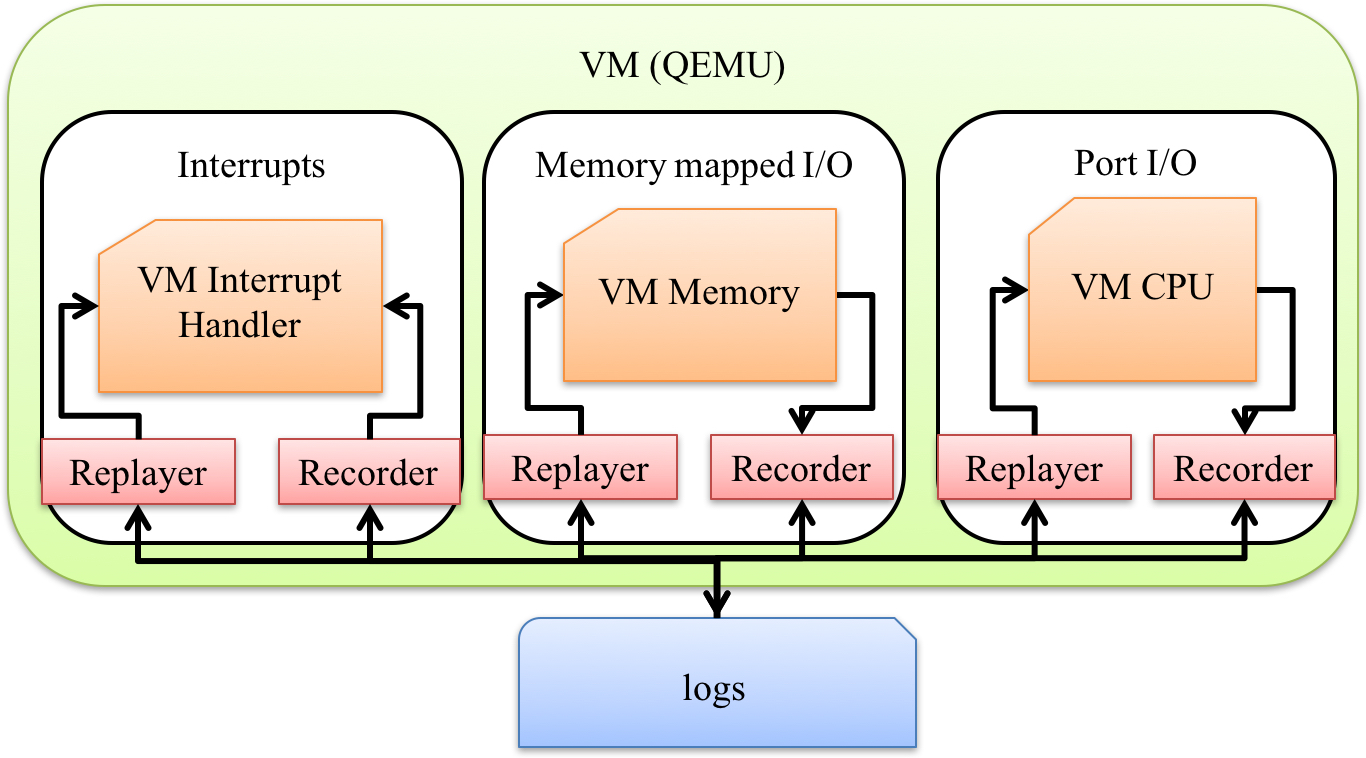
A Fine-grain Replaying VM Executions
Group Member: Chi-Wei Wang, Heng Yin
Replaying VM execution and the state transition of
systems is very useful for software testing, malware
analysis and post-attack recovery. We proposed a
generic VM-based logging and replaying mechanism.
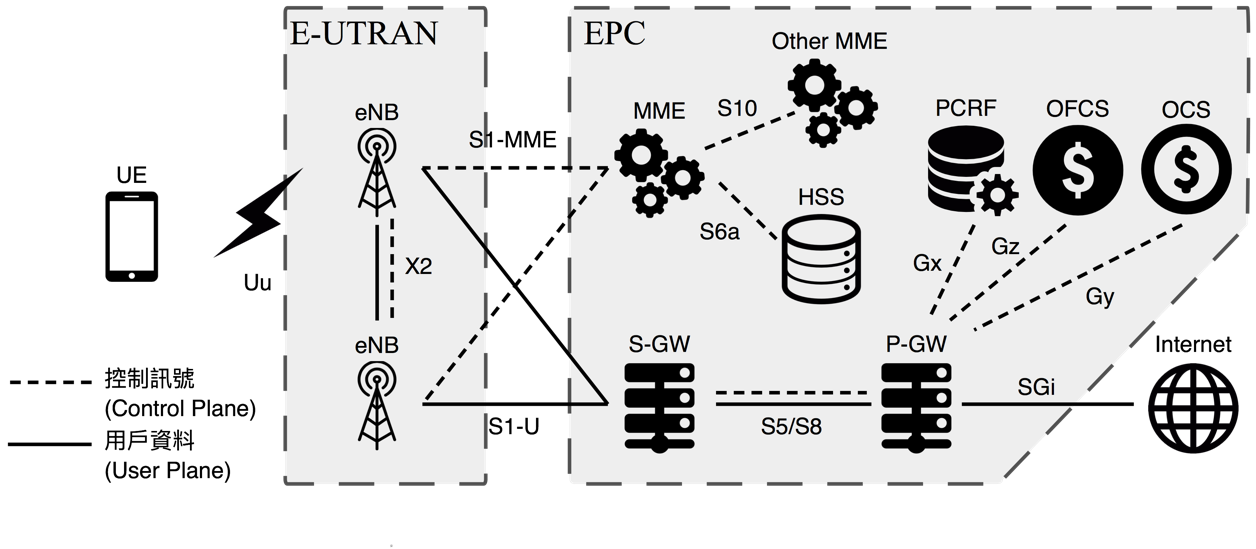
LTE Security
Group Member: Ting-Yi Chang, Yang-Ting Chiang
LTE brings IP packets into its core network. Conventional attacks via
IP network should be reviewed again in LTE. Moreover, HeNB, which is
connected via insecure network, will damage LTE security if no
essential security mechanism is not applied.
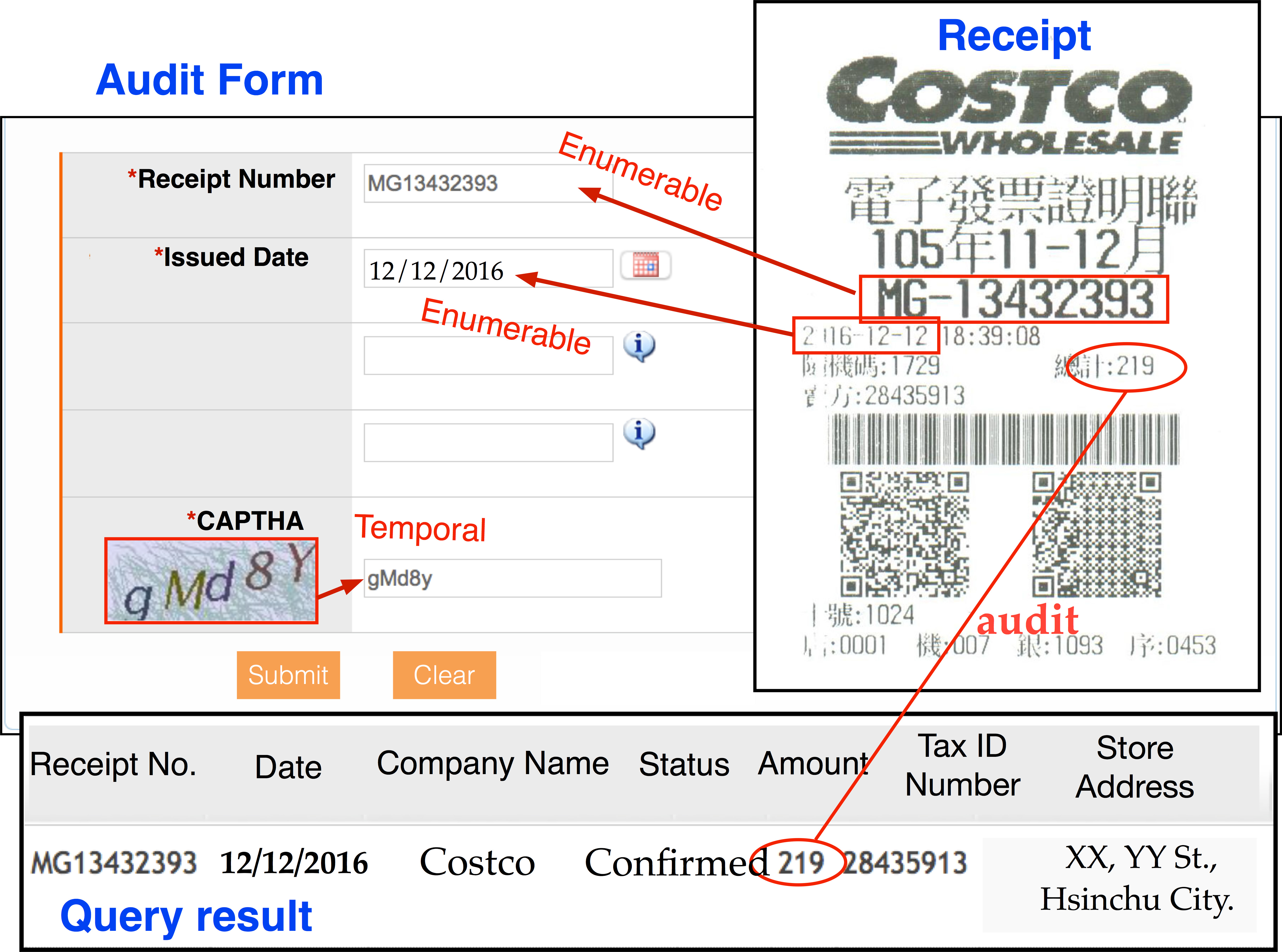
Aggregating Privacy from Online Data
Group Member: Chi-Pao Hung, Wei-Tse Tasi, Tzu-Jui Tung
A new kind of privacy leakage is devised through aggregating
public data to derive sensitive and private information. We
uncovered this kind of information leakage in practice and
will use the Taiwan Uniform Sales Receipt System (TUSR) as
an example to show the aggregation. Although the purchase
information on a sales receipt does not contain any sensitive
or private information, we will demonstrate in this paper
the data association technique of aggregating and deriving
a company’s revenue merely using a store sales receipt.
Publication
Journal
- Zong-Xian Shen, Chia-Wei Hsu, Shiuhpyng Shieh, “Security Semantics Modeling with Progressive Distillation,” IEEE Transactions on Mobile Computing, vol. 16, no. 11, pp. 3196–3208, Nov. 2017.
- Chia-Wei Hsu, Chia-Huei Chang, Chi-Wei Wang, and Shiuhpyng Shieh, “DROIT+: Taint Tracking for Storage Access on Android,” Journal of Information Science and Engineering (JISE), vol. 33, no. 5, pp. 1237-1254, 2017.
- Chia-Wei Hsu, Shan-Hsin Lee, and Shiuhpyng Shieh, “Adaptive Virtual Gestures for GUI Testing on Smartphones, ” IEEE Software, vol. 34, no. 5, pp. 22–29, 2017.
- Chia-Wei Hsu, and Shiuhpyng Shieh, “Mobile Security Survey and Trends,” Journal of Electrical Engineering, vol. 3, 2015.
- Michael Cho, Chia-Wei Hsu, and Shiuhpyng Shieh, C. W. Wang, “Can Malware be Exterminated by Better Understanding its Roots?,” IT Professional, vol. 16, no. 6, pp. 47–53, 2014.
- Jia-Chun Lin, Shiuhpyng Shieh, and Chia-Wei Hsu, “Proactive Distributed Digital Evidence Preservation with Tamper Resistance, Perfect Secrecy and High Survivability,” Journal of Information Science and Engineering (JISE), vol. 30, no. 6, pp. 1847–1864, 2014.
Conference
- Yang-Ting Jiang, Ting-Yi Chang, Chia-Wei Hsu, and Shiuhpyng Shieh,“Security Requirements and Risk Assessment for LTE Mobile Networks,“ in the 27th Cryptology and Information Security Conference (CISC), Taiwan, 2017.
- Liang-Mei Huang, Chien-Ho Chao, Chia-Wei Hsu, Shiuhpyng Shieh, and P. X. Liu, “Android app behavior analysis assessment and workflow design,” in the 26th Cryptology and Information Security Conference (CISC), Taiwan, 2016.
- Chun-An Shieh, Chia-Wei Hsu, Chien-Ho Chao, and Shiuhpyng Shieh, “Behavior Graph Construction of Android Apps,” in the 25th Cryptology and Information Security Conference (CISC), 2015.
- Zhi-Kai Zhang, Michael Cho, Chia-Wei Wang, Chia-Wei Hsu, Chung-Kuan Chen, and Shiuhpyng Shieh, “IoT Security: Ongoing Challenges and Research Opportunities, ” in IEEE 7th International Conference on Service-Oriented Computing and Applications (SOCA), pp. 230-234, 2014.
- Chia-Wei Hsu, Fan-Shun Shih, Chi-Wei Wang, and Shiuhpyng Shieh, ”Divergence Detector: A Fine-Grained Approach to Detecting VM-Awareness Malware." Software Security and Reliability (SERE), 2013 IEEE 7th International Conference on. IEEE, pp. 80-89, 2013.
- Ying-Chang Sung, Michael Cho, Chi-Wei Wang, Chia-Wei Hsu, and Shiuhpyng Shieh, “Light-Weight CSRF Protection by Labeling User-Created Contents,” in the IEEE 7th International Conference on Software Security and Reliability (SERE), pp. 60–69, 2013.
- Zong-Xian Shen, Chia-Wei Hsu, and Shiuhpyng Shieh, “Real-Time Record and Replay on Android for Malware Analysis,” in the 23th Cryptology and Information Security Conference (CISC), 2013.
- Chung-Kuan Chen, Wei-Chi Chen, Chia-Wei Hsu, and Shiuhpyng Shieh, “Mutant Malware Discovery and Behavior Analysis for Cyber Crime Investigation,” in the 22th Cryptology and Information Security Conference (CISC), 2012.
- Yen-Ru Liu, Chi-Wei Wang, Chia-Wei Hsu, Tsi-Chien Tseng, and Shiuhpyng Shieh, “Extracting Hidden Code from Packed Malware based on Virtual Machine Memory Comparison,” in the 21th Cryptology and Information Security Conference (CISC), 2011.
- Chia-Wei Hsu, and Shiuhpyng Shieh, "FREE: A Fine-grain Replaying Executions by Using Emulation", The 20th Cryptology and Information Security Conference (CISC), Taiwan, 2010. (Best Student Paper Award).
- Chi-Wei Wang, Chia-Wei Wang, Chia-Wei Hsu, and Shiuhpyng Shieh,,”Malware Behavior Analysis Based on Virtual Machine Introspection and Snapshot Comparison”, The 20th Cryptology and Information Security Conference (CISC), Taiwan, 2010.
Patent
- Shiuhpyng Shieh, Chi-Wei Wang, Chia-Wei Wang, Chia-Wei Hsu, Automatic probe construction system and method thereof, US, Appl. no. 15/016,120, 2017.
- Shiuhpyng Shieh, Chi-Wei Wang, Chia-Wei Wang, Chia-Wei Hsu, Automatic probe construction system and method thereof, Taiwan, Appl. no. I551984, 2016.
- Chi-Wei Wang, Chia-Wei Wang, Chia-Wei Hsu, Shiuhpyng Shieh, Chia-Huei Chang, Privacy leakage detection system and method, Taiwan, Appl. no. I578158, 2017.










